Explore the of NEM Wallet Desktop Application

Digital Signature

Multi-Signature Support

Advanced Encryption

Advanced Security Measures Protecting Your
- End-to-End Encryption: Securing your data from prying eyes.
- Multi-Factor Authentication: Adding an extra layer of security.
- Regular Security Audits: Ensuring continuous protection.
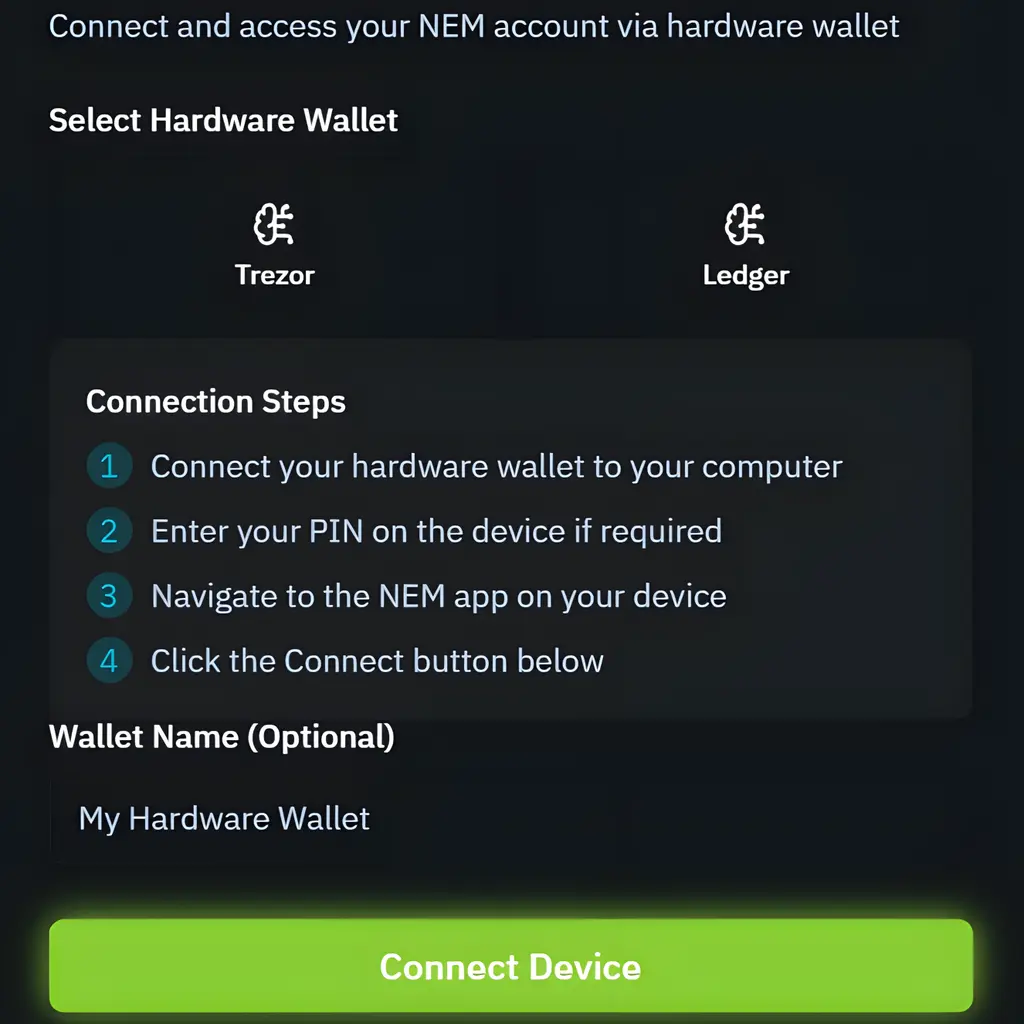
Seamless & Secure Access to the NEM Blockchain
Using a hardware wallet like Trezor or Ledger ensures your private key stays offline at all times. This means no exposure to malware, phishing attacks, or remote exploits. You maintain full ownership while interacting securely with the NEM network.
NEM’s delegated proof-of-stake model and modular design make it ideal for business applications. From tokenized supply chains to internal asset tracking, the blockchain delivers performance, reliability, and control at scale.
With NEM’s powerful mosaic and namespace system, users can create fully customized on-chain assets in just a few clicks. Define fixed or mutable supply, enable or restrict transfers, and choose how divisible your token is — whether it’s a coin, a utility token, or a digital certificate. Combine it with a namespace to give your asset a unique, recognizable identity across the entire blockchain. No smart contract coding needed, no risk of bugs — it’s all native, efficient, and built for scalability.
NEM lets you create and manage digital assets with ease, directly on-chain. You have full control over supply, transfer rules, and divisibility — no smart contracts needed. Whether it’s loyalty points, utility tokens, or certificates, everything is handled natively and securely.Namespaces let you assign your assets a clean, recognizable identity, making them easier to trust and integrate. It’s fast, efficient, and designed for real use — perfect for projects that value simplicity, security, and long-term scalability.
